Another day I was watching this video (link and player below) about ideas on how to detect injection attacks via CobaltStrike, which is such a powerful offensive testing solution. I realized that many of the ideas presented in the video somehow relate to SECRET papers; Here I explain how.
The first idea presented in the video is a solution that identifies some processes that were likely injected and dumps their page’s content for further inspection (as shown below). From what I get, the imagined scenario is manual analyst inspection, but one can easily imagine an extension to AV/EDR operation with automatic checks.
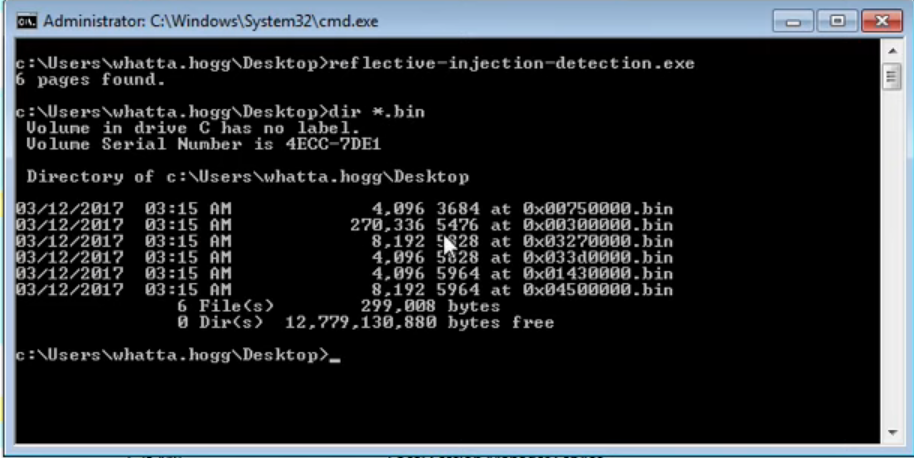
The video then shows how the tool works, by checking pages with RWX permissions, i.e., that can be written and executed, as shown below.
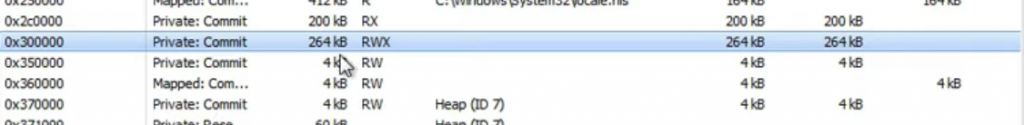
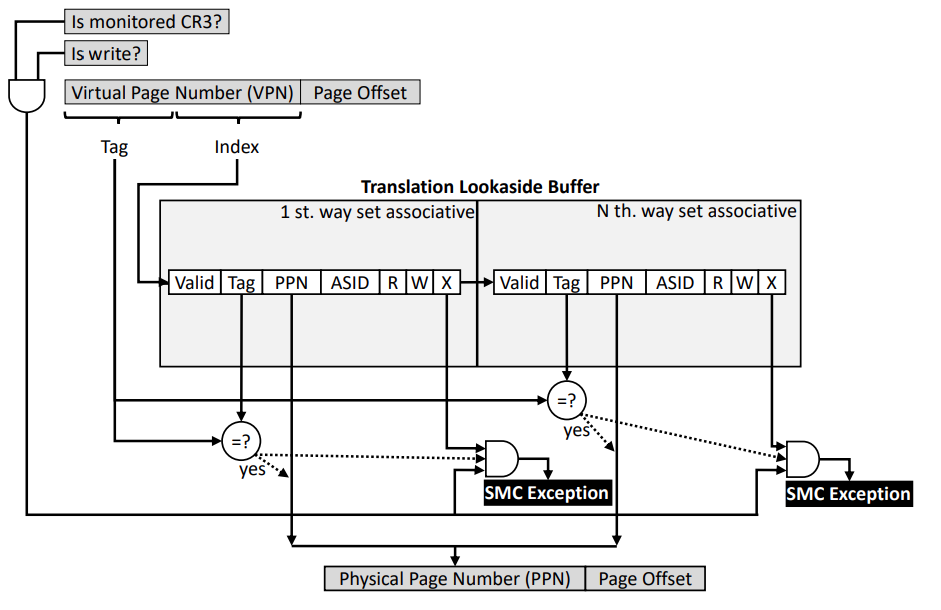
Well, that’s an interesting idea, but to do it automatically we need to continuously enumerate allocated pages and check their attributes. How to do it efficiently? i.e., without polling, without querying OS APIs all the time. It happens that SECRET has a paper on that (link here), in which we propose some hardware modifications to perform such checks in real-time and raise an interrupt to an AV/EDR only when a suspicious page is identified.
The first idea we proposed was to monitor the writing of an executable page and raise an exception when it happens, as shown below.
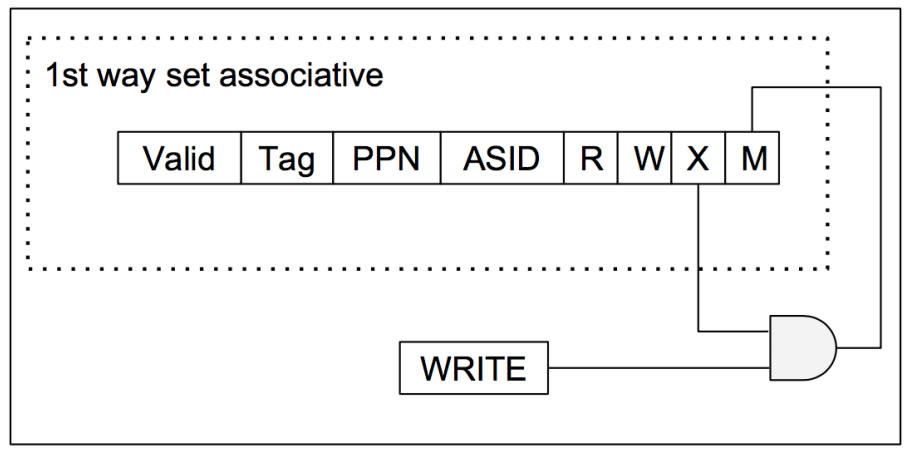
The second idea is to do the opposite: tracking executions of written pages (shown below). For such, we propose adding a modified (M) bit to the MMU in addition to the already-existing RWX. This would allow security notifications to be delivered via ordinary page faults (PFs).
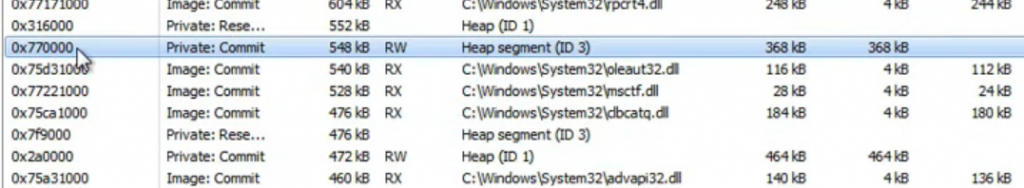
The video makes then a new suggestion of a more stealth technique: using RW pages only, now allocated in the heap (see figure below). This allows attackers to bypass RWX checks.
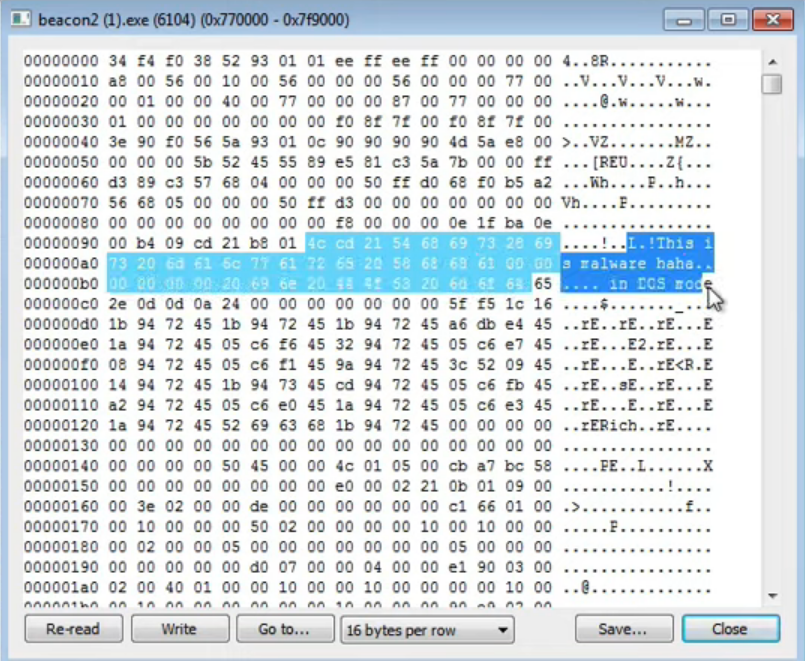
The video also shows that the payload is still there (see below), which sounds like a suggestion for adopting memory scans as a detection mechanism. But, again, how to do it efficiently? i.e., without reading all memory pages all the time?
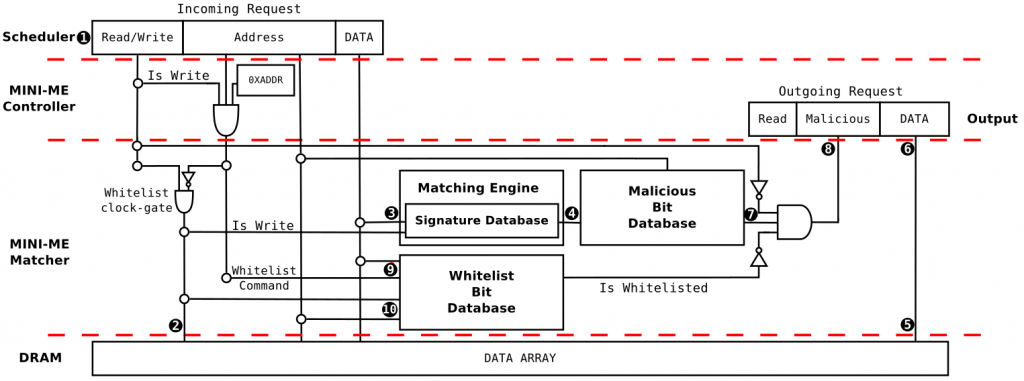
It happens that SECRET has a paper on that. The paper was accepted at MEMSYS (link) and is yet to be published (links will be added as soon as possible). In the paper, we propose a mechanism for scanning memory content within the memory chip, such that we can deliver malware detection information as soon as the memory content is requested by the processor (see the architecture below).
We believe that the adoption of such solutions would support stronger detection capabilities for AVs/EDRs. Are they the definitive solutions for the malware detection problem? Probably not; for instance, as attackers may move from RWX to RW page permissions in their attacks, they might also find ways to defeat in-memory checks in the future. Anyway, we believe that the adoption of this kind of technology might shape the way that attackers act, which is much better than the attacker’s operations shaping the way in which defensive solutions operate.
And will these solutions be really adopted? We can’t know. This is part of the academia-industry trade-off: Academia shows what we could theoretically do with technology and industry defines what can be actually deployed in customer’s machines. As part of academia, SECRET is here pointing to future possibilities, not dictating adoption rules. For vendors, delivering hardware modifications is always a hard task. Despite that, there are still interesting ideas that can be implemented in software, such as a better memory pages flag permission mechanism, thus allowing AVs/EDRs to better control software execution.
Does this research subject interest you? Get in touch with SECRET.


