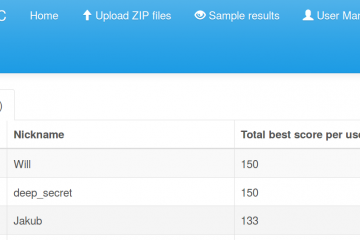
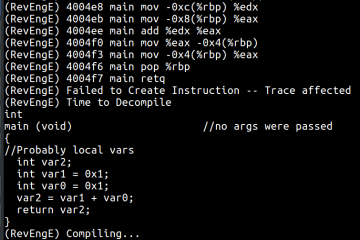
malware
Book Review: Using Science in CyberSecurity
In this post, I present my impressions of this book I recently read. Why Am I Reading It? To start, I think it’s important to give some context, as things cannot be interpreted absolutely. In the book’s preface, the authors state that the book is targeting a wide audience, from Read more…